
X.509 Certificates Explained: A Complete Guide to Digital Security Standards
X.509 certificates are digital credentials that manage identity and security in internet communications and computer networking. They're based on the ITU X.509 standard and use public key infrastructure (PKI) to enable secure communications.
How X.509 Certificates Work:
- Uses a public-private key pair for encryption and decryption
- Public key can be shared widely; private key remains secret
- Most commonly used in TLS/SSL for HTTPS protocol
- Enables secure web browsing, code signing, and digital signatures
Key Benefits:
- Establishes Trust:
- Verifies website authenticity
- Confirms organization identity
- Validates through trusted Certificate Authorities (CAs)
- Enables Scalability:
- Secures billions of daily messages
- Allows wide distribution of public keys
- Maintains security through private key protection
Certificate Components:
- Version number
- Serial number
- Algorithm information
- Issuer name
- Validity period
- Subject name
- Public key information
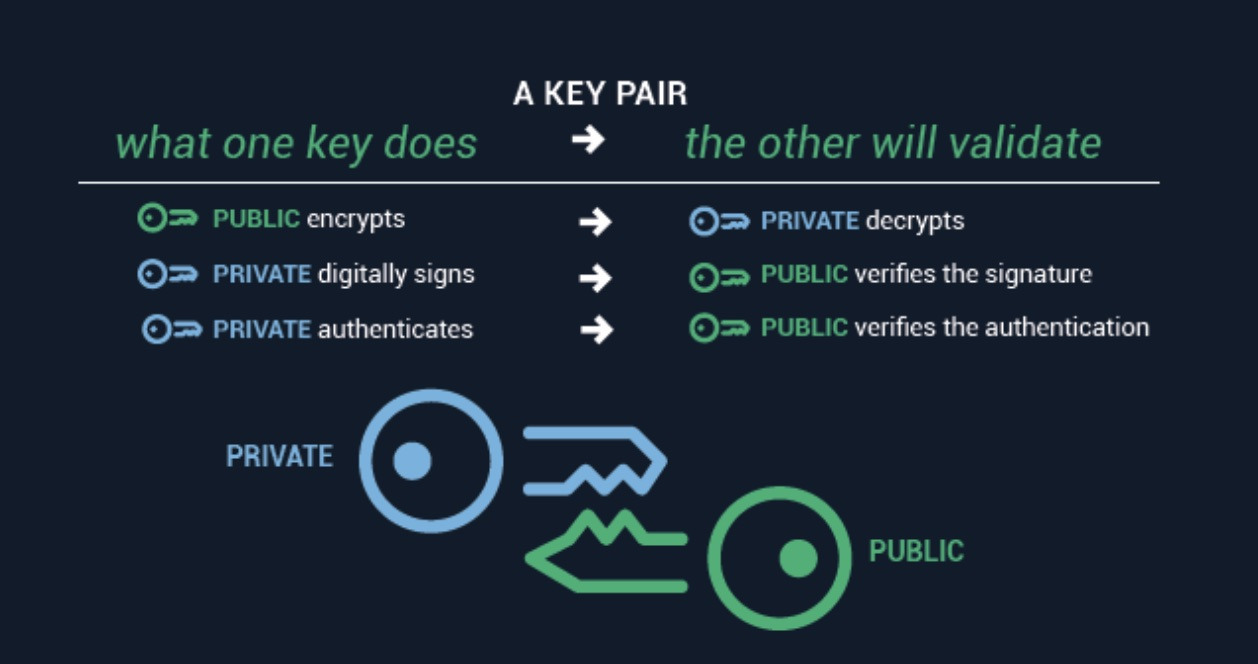
Private-public key encryption process
Common Applications:
- Web Security:
- SSL/TLS certificates
- HTTPS connections
- Protection against cyber attacks
- Digital Signatures:
- Document signing
- Identity authentication
- Message integrity verification
- Code Signing:
- Application security
- Software validation
- Developer authentication
- Email Security:
- S/MIME certificates
- Email encryption
- Sender validation
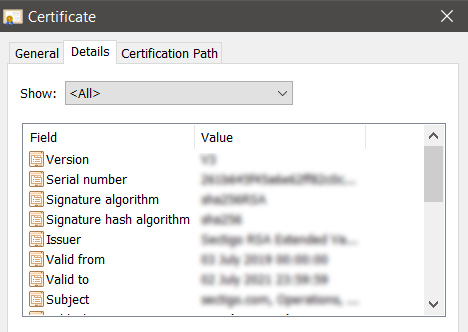
Certificate details dialog window
Trust Hierarchy:
- Certificates form a chain of trust
- Root CAs sign intermediate certificates
- Validation occurs through the entire chain
- Revocation lists track invalid certificates
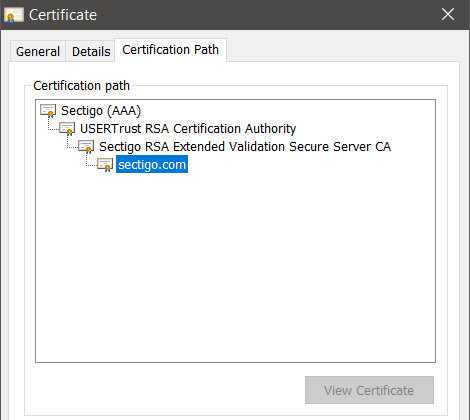
Digital certificate on laptop screen
To obtain an X.509 certificate, organizations can:
- Purchase from a trusted CA
- Set up their own CA
- Use self-signed certificates (limited trust)
Effective certificate management requires:
- Regular monitoring
- Automated lifecycle management
- Proper security controls
- Timely renewal and revocation
Related Articles
Timing Attacks: The Hidden Threat to Post-Quantum Cryptography Security

